VPN Exploit Allows Threat Actors to Read “Encrypted” Traffic
Researchers from Leviathan Security Group which focuses on penetration testing and security research have discovered a VPN exploit that allows threat actors to “read, drop or modify the leaked traffic” (Goodin). A VPN (virtual private network) is often used in public spaces to encrypt a user’s data so other users on the same network cannot interact with it. However, this exploit named TunnelVision can bypass a VPN’s encryption without alerting the user.
Imagine you are at a coffee shop grabbing a quick coffee while using your laptop to get work done. Your laptop is connected to the shop’s Wi-Fi via a DHCP server that assigns your laptop an IP address. For security your VPN is enabled to encrypt your traffic on a special virtual interface. Normally you are safe and secure ready to work. However, a threat actor could be reading your data without you ever knowing.
The researchers explain that first a threat actor on the same network could starve the DHCP server by using a program to collect all available IP address leases and auto renew them for themselves (Goodin). This prevents devices, including your laptop, from connecting to the real DHCP server. Next the threat actor uses their device as a malicious DHCP server and uses a DHCP option called option 121 to “set a route on the VPN user’s routing table” (Goodin). This means that the malicious DHCP server is creating a route on your laptop that is chosen by the threat actor. DHCP option 121 allows for the assignment of a static route which means the threat actor chooses the exact IP address that all data is routed to. In this case the threat actor would set their malicious DHCP server as the gateway that your laptop routes too. To bypass your VPN’s virtual interface threat actors push “routes that are more specific than a /0 CIDR range that most VPNs use” (Goodin). This creates routes that are higher priority than the virtual interface VPNs create. With your laptop now routing unencrypted traffic through the malicious DHCP server using option 121 the threat actor can “read, drop or modify the leaked traffic” (Goodin). Below is a graphic of what this would look like.
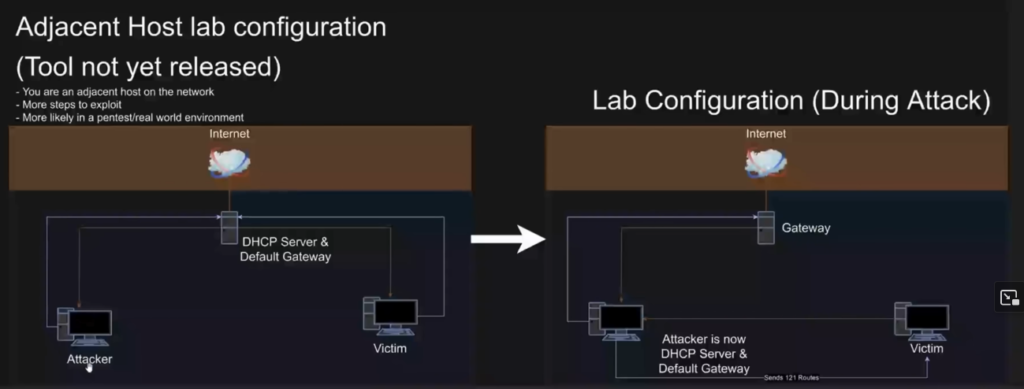
On the left your laptop is properly connected to the real DHCP server which provides your laptop with an IP address and a secure default gateway. On the right the threat actor has successfully established a malicious DHCP server that your laptop is now connected to and routing unencrypted traffic through before it is sent to the real server’s gateway. The victim would never know that they connected to a malicious DHCP server or that their data was being interacted with, as the VPN will show no errors and “always [continue] to report as connected” (Goodin).
The TunnelVision attack can be easily carried out by a network administrator or even an every day threat actor who sets up a rogue DHCP server. This means that any public Wi-Fi is vulnerable to an individual running this attack.
This attack is extremely dangerous and worrisome to VPN users, as it can completely expose sensitive data and negates the entire point of using a VPN. Users on public Wi-Fi and any device except for android are vulnerable to this attack. Android does not use option 121, so it is safe from this attack. Otherwise the best way to avoid this attack is to connect “through the Wi-Fi network of a cellular device” (Goodin). It is important to keep yourself and your information protected, so for now it may be dangerous to trust your VPN on a public Wi-Fi.
Continue Reading This Story
Goodin, Dan. “Novel Attack against Virtually All VPN Apps Neuters Their Entire Purpose.” Ars Technica, 6 May 2024, arstechnica.com/security/2024/05/novel-attack-against-virtually-all-vpn-apps-neuters-their-entire-purpose/.